
|
Boxiang Dong, Ph.DAssociate Professor Department of Computer Science Montclair State University Office: CCIS 327R Phone: 973-655-4093 Email: dongb AT montclair DOT edu |

|
Boxiang Dong, Ph.DAssociate Professor Department of Computer Science Montclair State University Office: CCIS 327R Phone: 973-655-4093 Email: dongb AT montclair DOT edu |
I am an associate professor in the Computer Science Department at Montclair State University.
Prior to joining MSU, I received my Ph.D in Computer Science in 2016 from Department of Computer Science of Stevens Institute of Technology, which is located in NJ, USA. My Ph.D advisor is Prof. Wendy Wang. The title of my Ph.D dissertation is "Privacy-preserving and Authenticated Data Cleaning on Outsourced Databases" [PDF] [Slides].
In 2011, I received my Bachelor degree from Dalian University of Technology, China. In that time period, I worked with Prof. Weifeng Sun on network security.
This is my CV (last updated: 10/2021).
| 2023-03 | Our paper has been accepted by Creativity Research Journal! |
| 2023-01 | Our REU summer program is accepting new applications for Summer 2023. Website! |
| 2022-09 | I have been promoted to tenured and associate professor at MSU! |
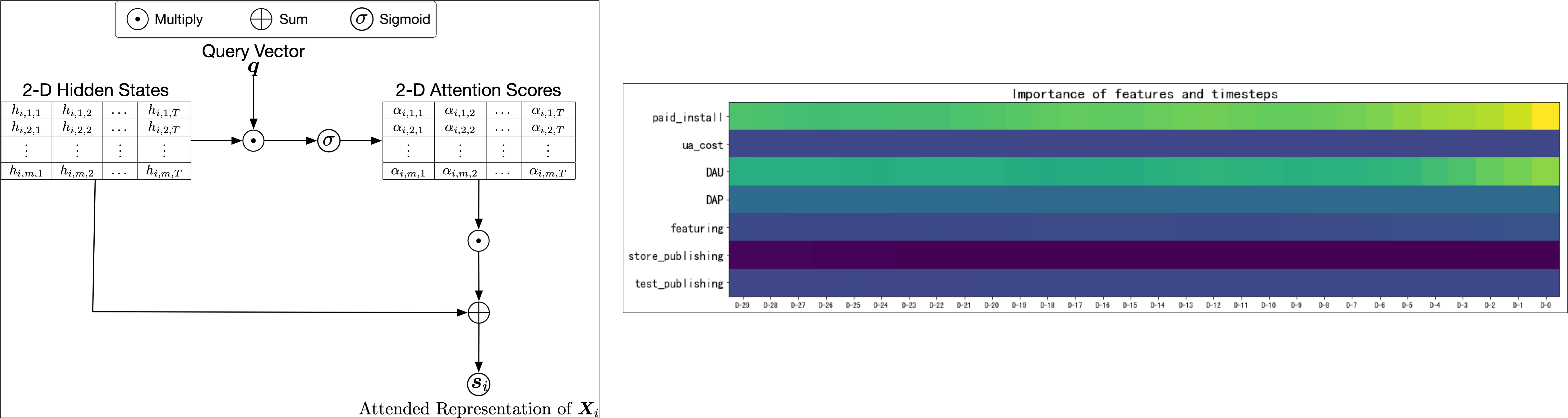
We propose a novel attention mechanism to reveal the information flow in the generative process of the target variable and quantify the contribution of each factor.
The evaluation on mobile gaming datasets discover sparkling knowledge about the driving factors of organic installs.
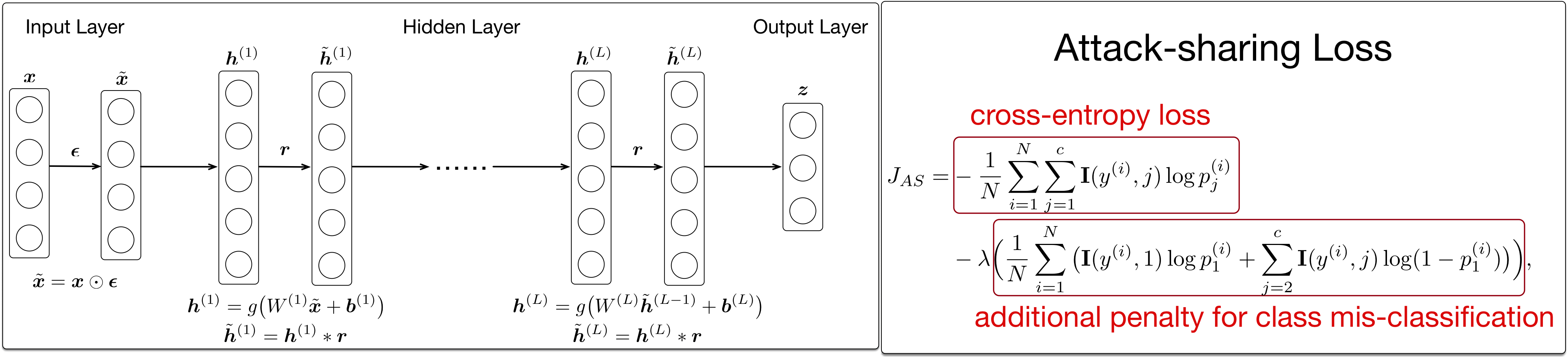
We propose a deep neural network infrastructure to detect network intrusion attacks.
To cope with the imbalanced distribution of various types of attacks, we propose a novel loss function that eliminates the bias towards the majority class.
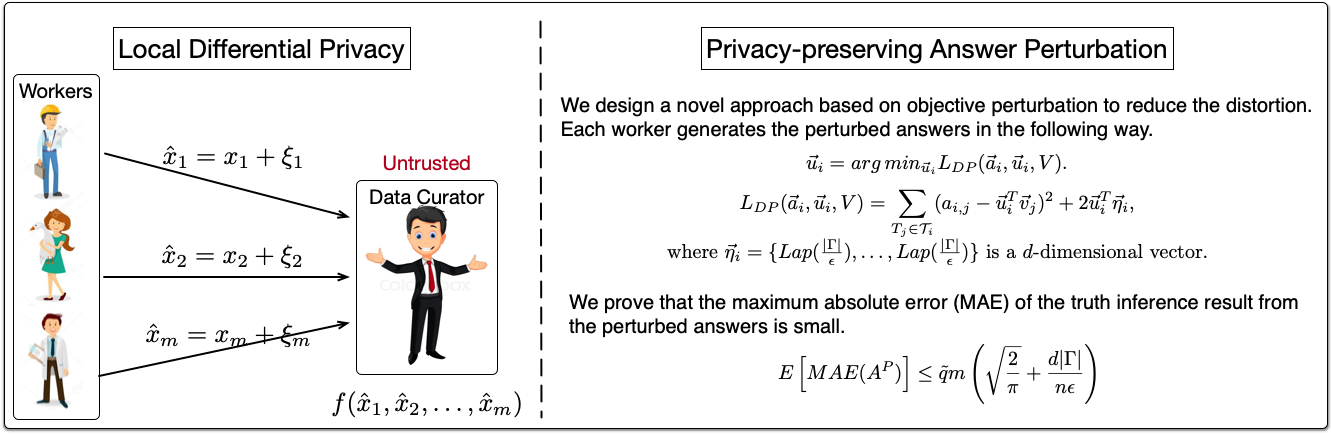
We protect the privacy in the setting of crowdsourcing in two ways.
First, we protect task privacy by designing a task assignment strategy that minimizes the risk of information disclosure in the existence colluding workers.
Second, we protect worker privacy by designing an answer perturbation mechanism to provide local differential privacy.
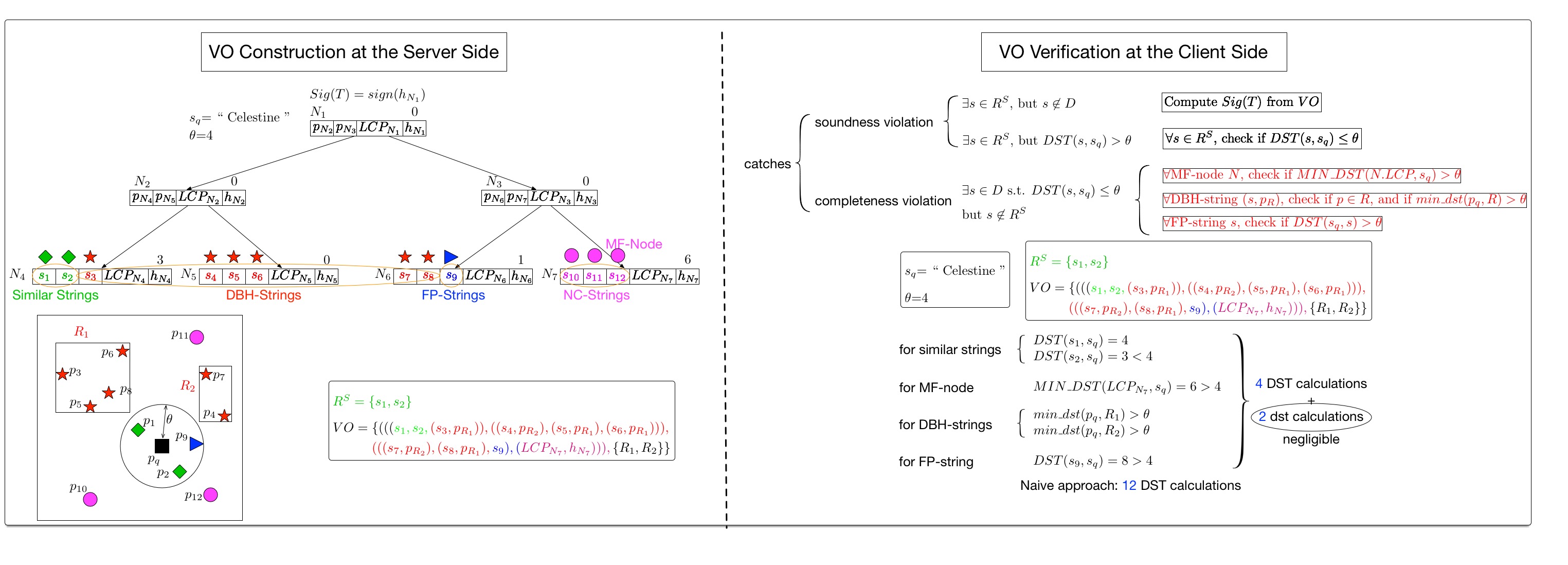
We design a new authentication and indexing data structure--Merkle Bed Tree (MB-Tree in short), which obtains Merkle tree's authentication functionality and preserves Bed tree's indexing property.
The server constructs verification objects (VOs) by traversing the MB-Tree and visiting the Euclidean space to prove the result's soundness and completeness.
The client's verification cost is very small because of MB-tree's pruning power and the cheap Euclidean distance computation cost.
We define two security models: &alpha-security against frequency-analysis attack, and indistinguishability against functional dependency preserving chosen plaintext attack (IND-FCPA).
We design a frequency-hiding FD-preserving probabilistic encryption scheme that provides strong security guarantee, while preserves the utility in the encrypted dataset.
We model the system events in every host as a multipartitie graph of interactions between processes, sockets, and files.
We apply random walk on the graph to learn the routine behavior of each system entity based on a transition probability model.
We label an event sequence as abnormal if the behavior of any involved entity largely deviates from its routine role.
In order to defend against the frequency-analysis attack in the outsourced data-deduplication services, we propose two approaches.
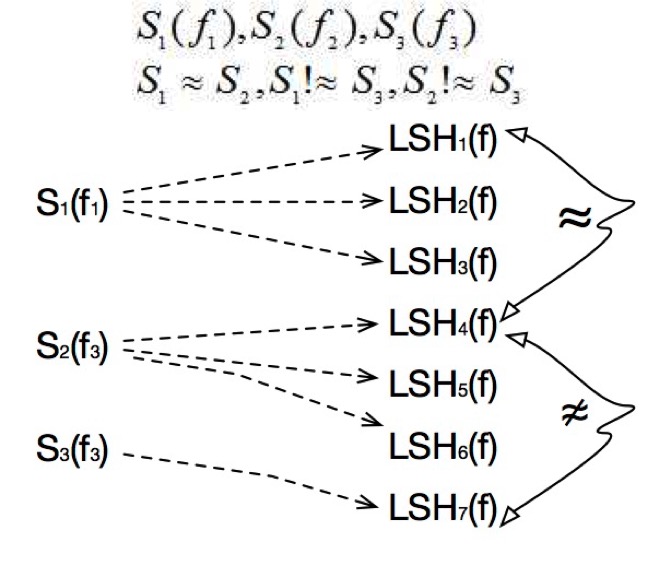 |
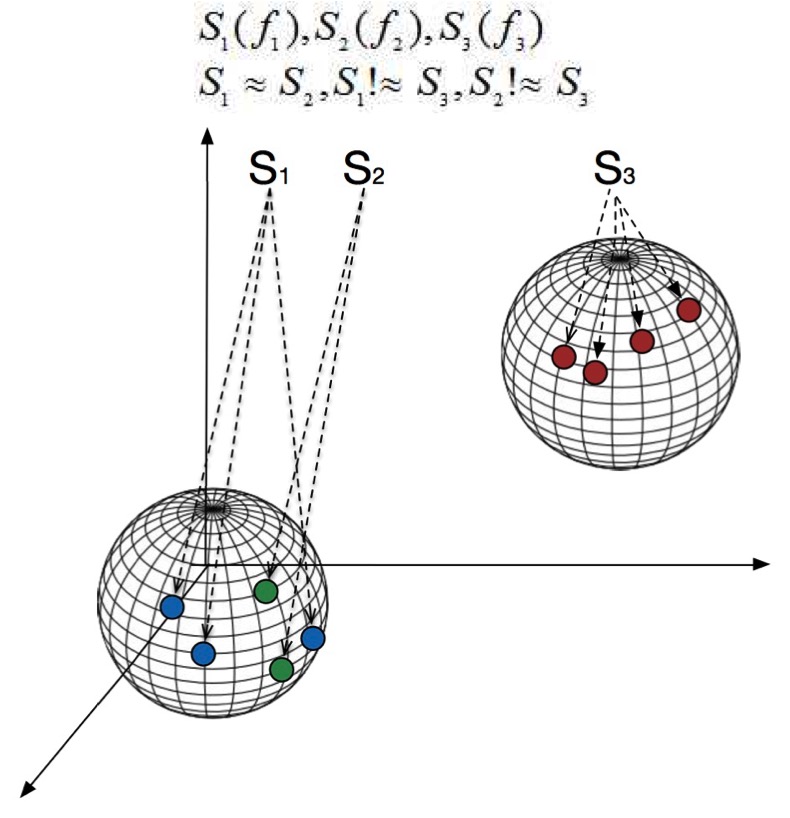 |
| LSHB approach | EHS approach |
We aim at verifying if the untrusted server returns the correct and complete frequent itemset mining result.
To accomplish the goal, we require the server to return cryptographic proofs to show the support of the itemsets. The proof is based on the Secure Set Intersection Protocol.
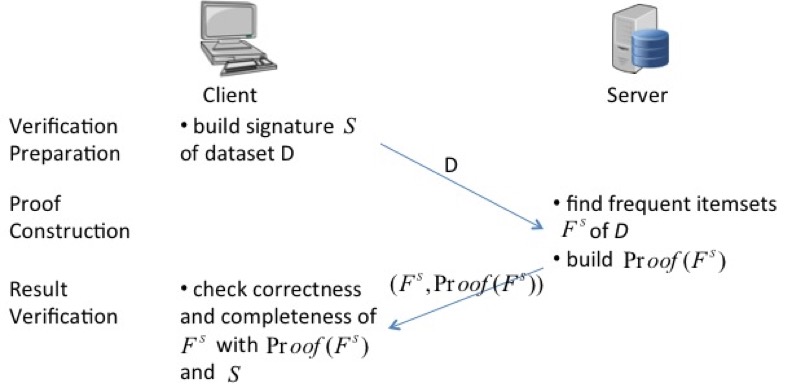
Related publications:
CSIT212 Data Structures and Algorithms Fall 2017, 2018, Spring 2018
CSIT111 Fundamentals of Programming I Fall 2017
CSIT100 Introduction to Computer Science Spring 2017
CSIT345 Operating Systems Spring 2017
Introduction to Cybersecurity (part of Stevens Pre-College Programs) Summer 2016
|
Sep.2022 - Now
|
|
Jan.2017 - Aug.2022
|
|
Sep.2014 - Dec.2014
|
|
May.2015 - Aug.2015
|